- Home
- X Platform
- Security
All parts of the EXOR X Platform sit as a working bridge between the need for high levels of security and the usability of an IIoT system. There is by necessity a compromise to be made between these two sides.
With Corvina, administrators will be able to simply and securely access , monitor and manage all network connected devices. Managing the balance will be made far more efficient and effective as a result.
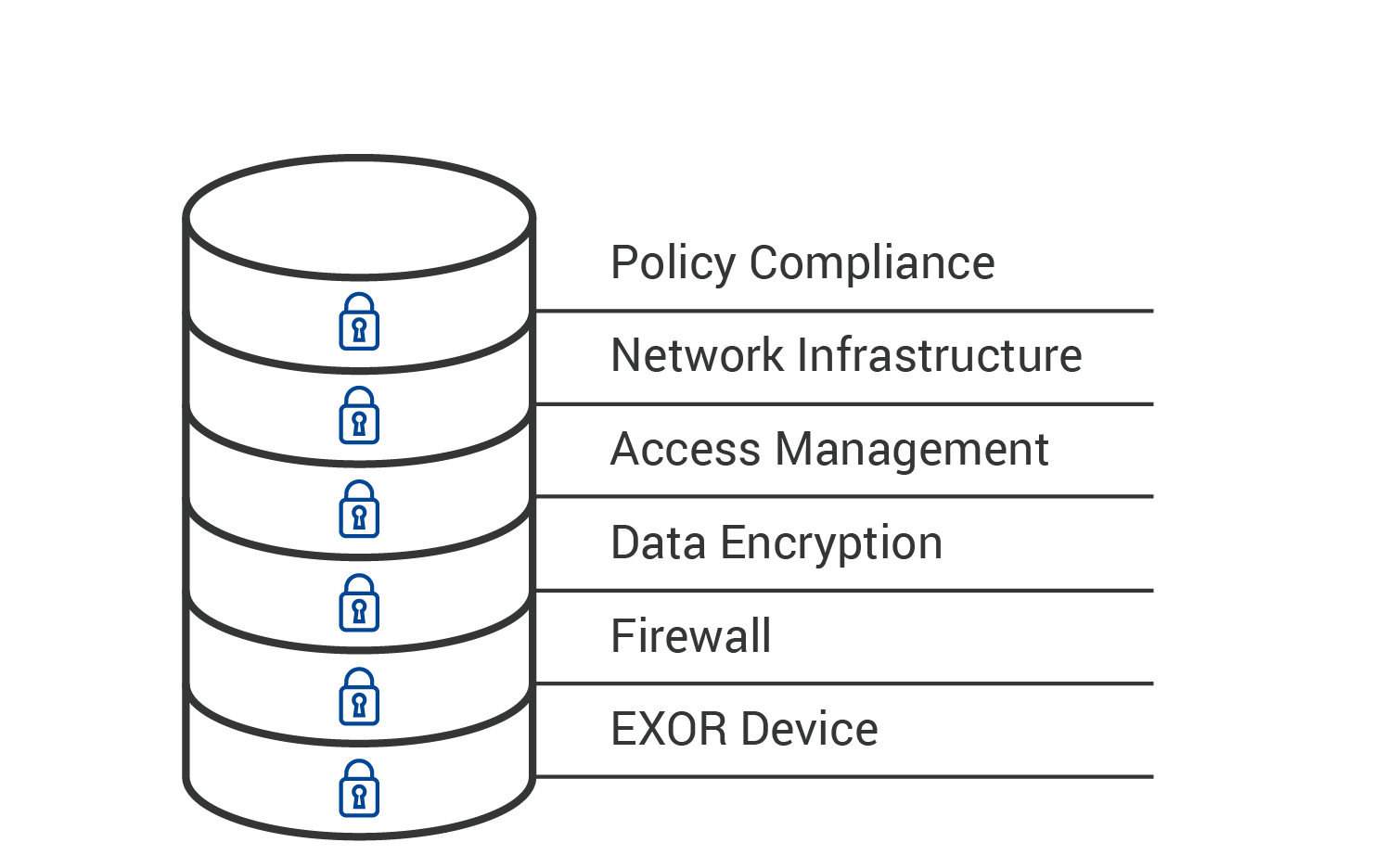
Layered Security
EXOR’s approach to security is based on the international guidelines set out in:
- IEC 62443
- NIST Cyber security Framework 1.0
Akin to the nascent industry standard EXOR has multiple layers of security that allow as much as possible our clients to be protected but at the same time can actually go about their business.
The security has to present and robust but not impede operational needs. This is the delicate balancing point which we work with each of our clients to achieve.
Firewall
IP, port, and protocol filtering/firewalling available. Restricted access based on user, group, site for all or single devices.
With the combined set up features of Organization and User Management administrators are afforded complete flexibility over filtering and firewall rules. Devices, users, departments, and even individual I/O ports can all be configured.
Firewall settings are 100% configurable to the organization and department needs this ensuring that the company is able to operate effectively. Access to the devices IP address, ports, FTP and HTTP servers can all be configured.
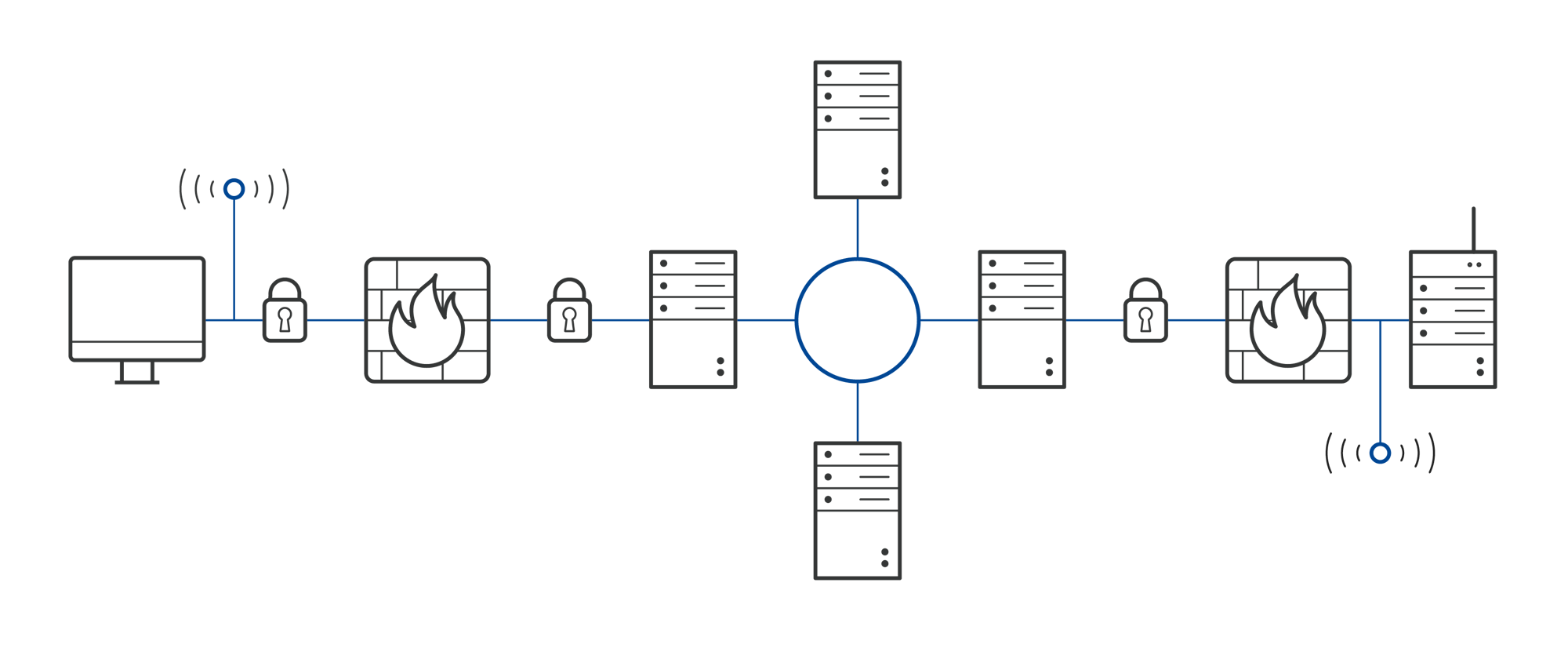
Traffic Encryption
VPN sessions are end-to-end encrypted using SSL/TLS protocol
Communications between the remote user and the device are fully encrypted using the SSL/TLS protocol, ensuring data authenticity, integrity & confidentiality.
All users and EXOR devices are authenticated using x509 SSL certificates and end-to-end traffic is encrypted using strong symmetric & asymmetric algorithms that are part of the SSL/TLS protocol cipher suite.

User and Access Management
Unique user logins, configurable user rights to different devices, two-factor authentication, connection traceability
There is no limit to the number of users that can be applied to the xCloud account. Unique logins may be created for every user and as such it is easy to alter and revoke access as and when needed.
Administrators have complete control, allowing them to direct access of engineers for re programming or updating of software whereas simple monitoring access for factory floor managers.
In a recent survey commissioned by IBM, they pointed out that over 495 of old employees maintain their access credentials even after leaving the company.
With the cloud based soulutions of EXOR this risk is now easily eliminated.
All access, all traffic and all remote access can be documented as a report. This provides the final “manual” check that the right users have access to the right levels.
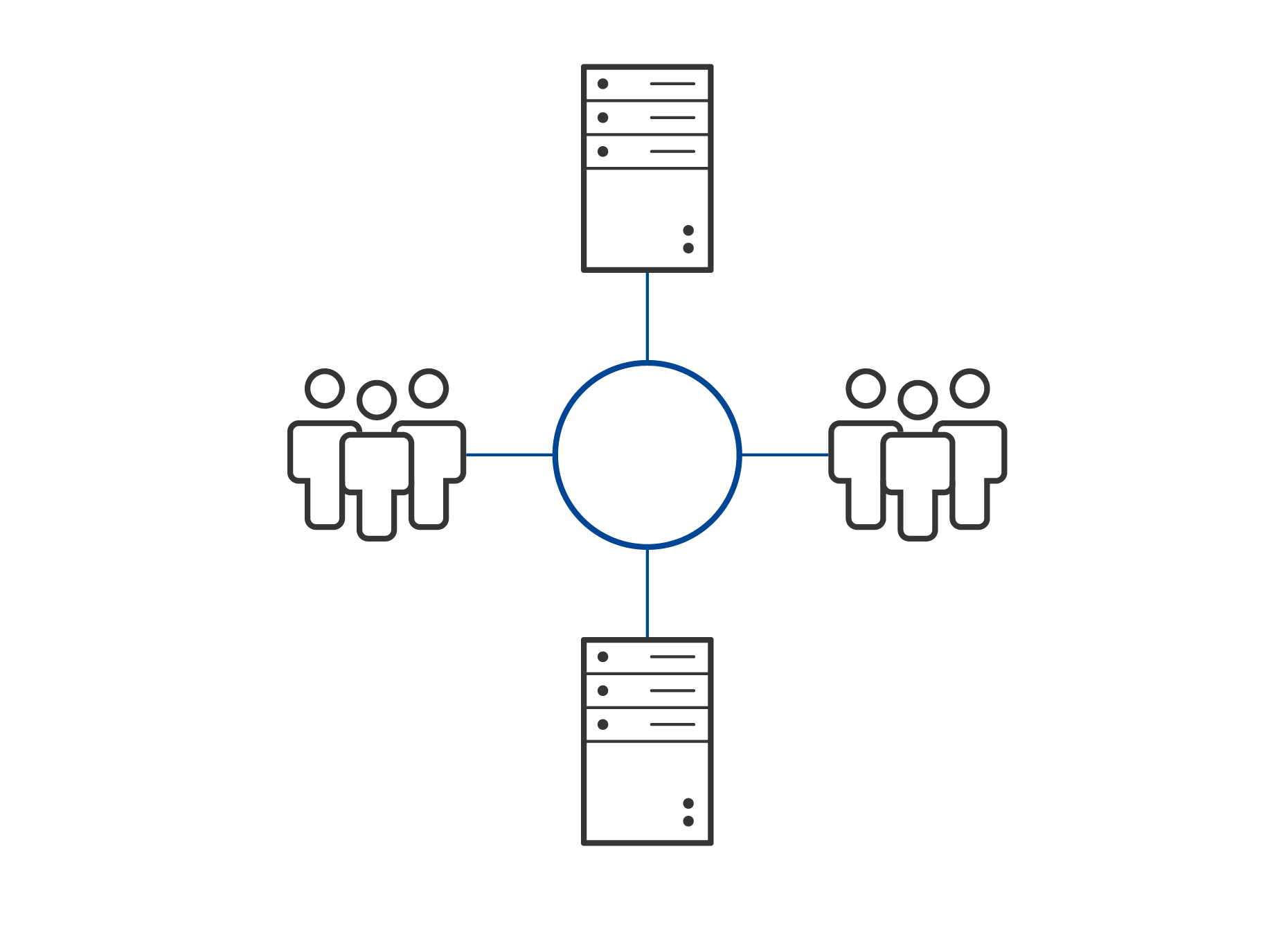
Network Infrastructure
The EXOR cloud based solutions layered infrastructure plays an important role in all our remote access solutions. It brings together in a secure data area all network servers, VPN servers and any other service.
EXOR partners with leading global Tier 1, 2 and 3 hosting partners to reduce and define latency. Having a defined latency is one of the critical requisites of Industrial IoT.
Management of Security
The security of our products and systems is a priority.
If you've identified a potential vulnerability, collaborating responsibly is the best way to protect them.


